Server names can include an asterisk replacing the first or last part of a name. 3 Normative References 4 Overview 41 Web Scripting.

What Is A Proxy Server How They Work List Of Security Risks Upguard
From command line using repo source.

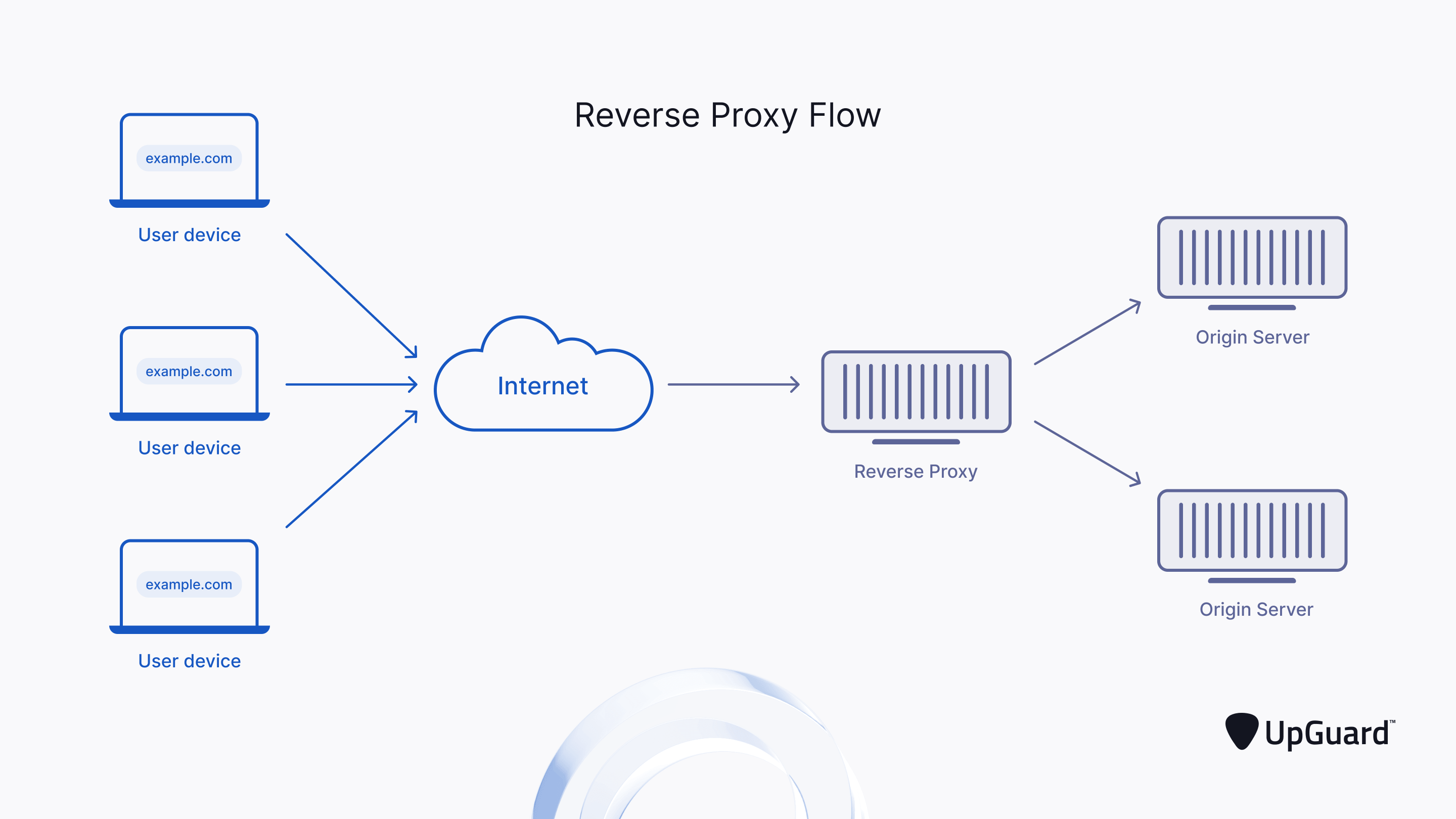
. You never needed a passphrase to load a certificate but you need one to load your private key. RFC 7231 HTTP11 Semantics and Content June 2014 corresponding request-line and header section to the next inbound server. A reverse proxy is a web server that centralizes internal services and provides unified interfaces to the public.
Kestrel used as an edge Internet-facing web server. See flags for full list of available configuration options. You can use the following environment variables to proxy HTTP and HTTPS requests.
Default props props mergeProps name. Component Object Model COM is a binary-interface standard for software components introduced by Microsoft in 1993. However proxy can refer to any resource along a path hierarchy while custom refers to a particular path segment only.
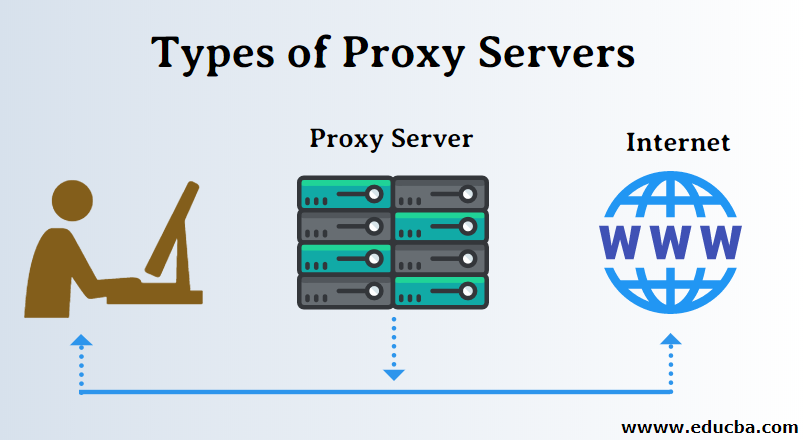
A definition of proxy server with common examples. Internet Information Services IIS Nginx. These are most commonly used to map human-friendly domain names to the numerical IP.
This method works by using a proxy and resolving properties in reverse order. Yet Another Reverse Proxy. A reverse proxy server receives HTTP requests from the network and forwards them to Kestrel.
A virtual private network VPN extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Proxypy also tried to set open file limit ulimit on the system. Such names are called wildcard names.
Practice common system design interview questions and compare your results with sample solutions. As other tree-based data structures the searching algorithm requires a comparison function that returns -1 0 or 1 for any pair of keys domain names. This allows for dynamic tracking of properties that arent present when the prop object is first merged.
User authentication via external processes. Learn how to improve power performance and focus on your apps with rapid deployment in the free Five Reasons to Choose a Software Load Balancer ebook. Kestrel used in a reverse proxy configuration.
The field was fundamentally established by the works of Harry Nyquist and Ralph Hartley in the 1920s and Claude Shannon in the 1940s. This improves performance and also allows a service to continue to function when a server goes down. Each service instance is paired with an instance of a reverse proxy server called a service proxy sidecar proxy or sidecar.
答案 Proxy 代理是ES6新增的功能可以理解为代理器即由它代理某些操作 Proxy 对象用于定义或修改某些操作的自定义行为可以在外界对目标对象进行访问前对外界的访问进行改写. Object object function Proxying some URLs can be useful when you have a separate API backend development server and you want to send API requests on the same domain. 42 Hosts and Implementations 43 ECMAScript Overview 431 Objects.
This prevents web servers from becoming overloaded by quickly. 432 The Strict Variant of ECMAScript 44 Terms and Definitions 441 implementation-approximated. Interpretation of ACL-driven directives is based in part on the following rules.
For example a grocery store might organize its online product inventory by department names produce categories and product. The benefits of a VPN include increases in functionality security and management of the private networkIt provides access to resources. When HTTP_PROXY http_proxy are set they will be used to proxy non-SSL requests that do not have an explicit proxy configuration option present.
The resource records contained in the DNS associate domain names with other forms of information. If your proxy server has several network interfaces sometimes you might need to choose a particular source IP address for. A DN Distinguished Name syntax attribute in Active Directory whose value is based on a Link Table and the value of a related forward link attribute.
It is common for microservices architectures to be adopted for cloud-native. As we can see before starting up. Default value for --open-file-limit used is 1024--open-file-limit flag is a no-op on Windows operating systems.
Both the proxy resource of proxy and the custom resource of custom are expressed as templated path variables. If you are trying to run proxypy from source code there is. Requests from clients are forwarded to a server that can fulfill it before the reverse proxy returns the servers.
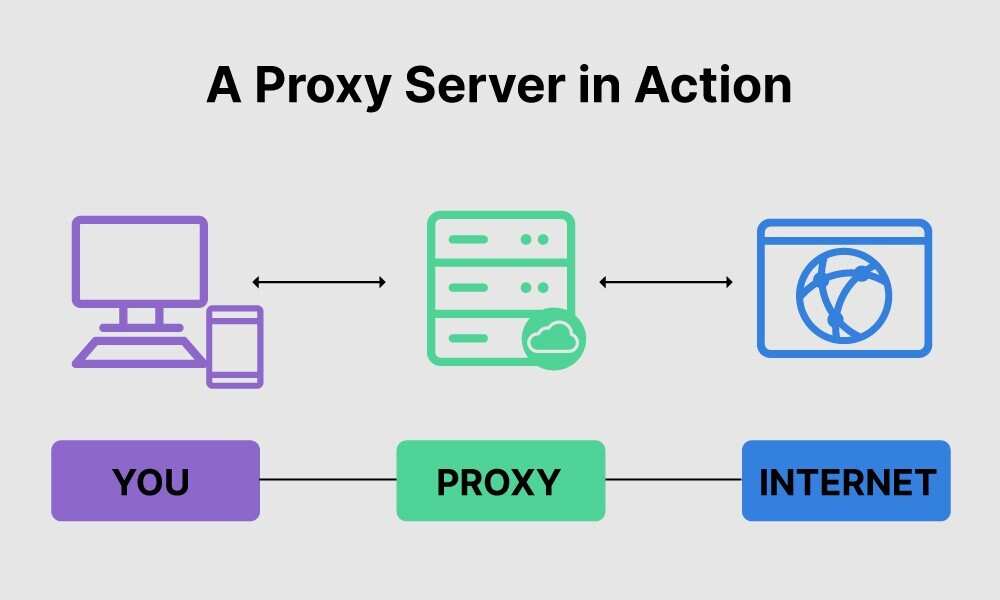
A proxy server may reside on the users local computer or at any point between the users computer and destination servers on the InternetA proxy server that passes unmodified requests and responses is usually called a gateway or sometimes a tunneling proxyA forward proxy is an Internet-facing proxy used to retrieve data from a wide range of sources in most. Set the string be used as the password required to use the CURLOPT_PROXY_SSLKEY private key. Geonode API plays nice with many common languages such as PHP Python Net Java JavaScript CC and C.
Clone props newProps mergeProps props. The Domain Name System DNS is the hierarchical and decentralized naming system used to identify computers reachable through the Internet or other Internet Protocol IP networks. Merge props props mergeProps props otherProps.
If the proxy believes from configuration or past interaction that the next inbound server only supports HTTP10 the proxy MAY generate an immediate 100 Continue response to encourage the client to begin sending the. Check out its documentation for more advanced usages. The code snippet above exports a function to the application so that the proxy middleware is registered to the application as soon as the development server starts up without the need to import it.
It is used to enable inter-process communication object creation in a large range of programming languagesCOM is the basis for several other Microsoft technologies and frameworks including OLE OLE Automation Browser Helper Object. A common use of a reverse proxy is to provide load balancing. ACM Transactions on Recommender Systems TORS will publish high quality papers that address various aspects of recommender systems research from algorithms to the user experience to questions of the impact and value of such systemsThe journal takes a holistic view on the field and calls for contributions from different subfields of computer science and.
The dev-server makes use of the powerful http-proxy-middleware package. Information theory is the scientific study of the quantification storage and communication of information. The field is at the intersection of probability theory statistics computer science statistical mechanics information engineering.
This option is for connecting to an HTTPS proxy not an HTTPS server. Examples of a reverse proxy server include. Alternative approaches must be considered - such as packaging the function as a library moving the function into other microservices.
The first name becomes the primary server name. The realization that data is becoming so important in the world and that there was definite room for improvement in the proxy space. While we pride ourselves on our developer friendliness we envision a future where data collection.
Acronym for Backup Domain ControllerIn NT domains there was. For example the member attribute of group objects is the forward link while the memberOf attribute is the related back link. There are two common approaches of setting up proxy servers in React applications developed using CRA.
Available since PHP 730 and libcurl cURL 7520. How to set up a proxy server in React. Caching Proxies that cache static content for websites such as videos images scripts and html.
1 Scope 2 Conformance 21 Example Clause Heading.

Lesson 4 Web Browsing Ppt Download Lesson Name Server Proxy Server
What Is A Proxy Server How They Work List Of Security Risks Upguard
0 Comments